[ #003 ] NMaaS-101 - "My name is Oxidized and I'm a nifty configuration management tool"
In article #001 and #002 you essentially created a NMaaS domain and enabled connectivity between your dedicated and isolated domain to your out of band management equipment network.
Requirements
Overview
We are going to deploy our first NMaaS service for your organisation: Oxidized
Article objective
This is done in 2 steps:
- Oxidized application deployment via the NMaaS portal
- Oxidized configuration specific to RARE domain
Diagram
[#003] - Cookbook
Oxidized application deployment
- Once your domain is created and associated to your account, log into https://nmaas.eu as in #001
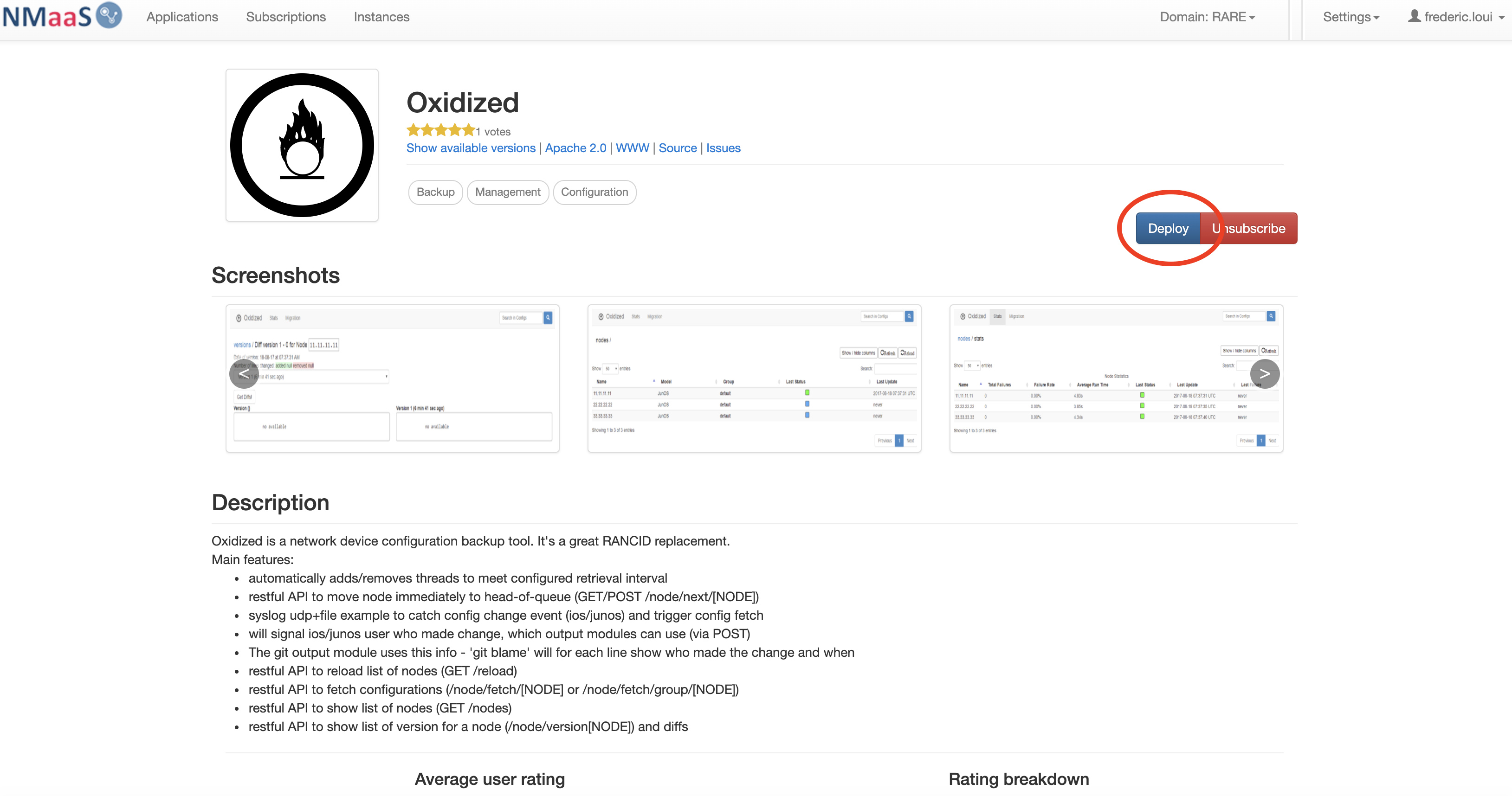
- select Oxidized application
- select "Deploy"
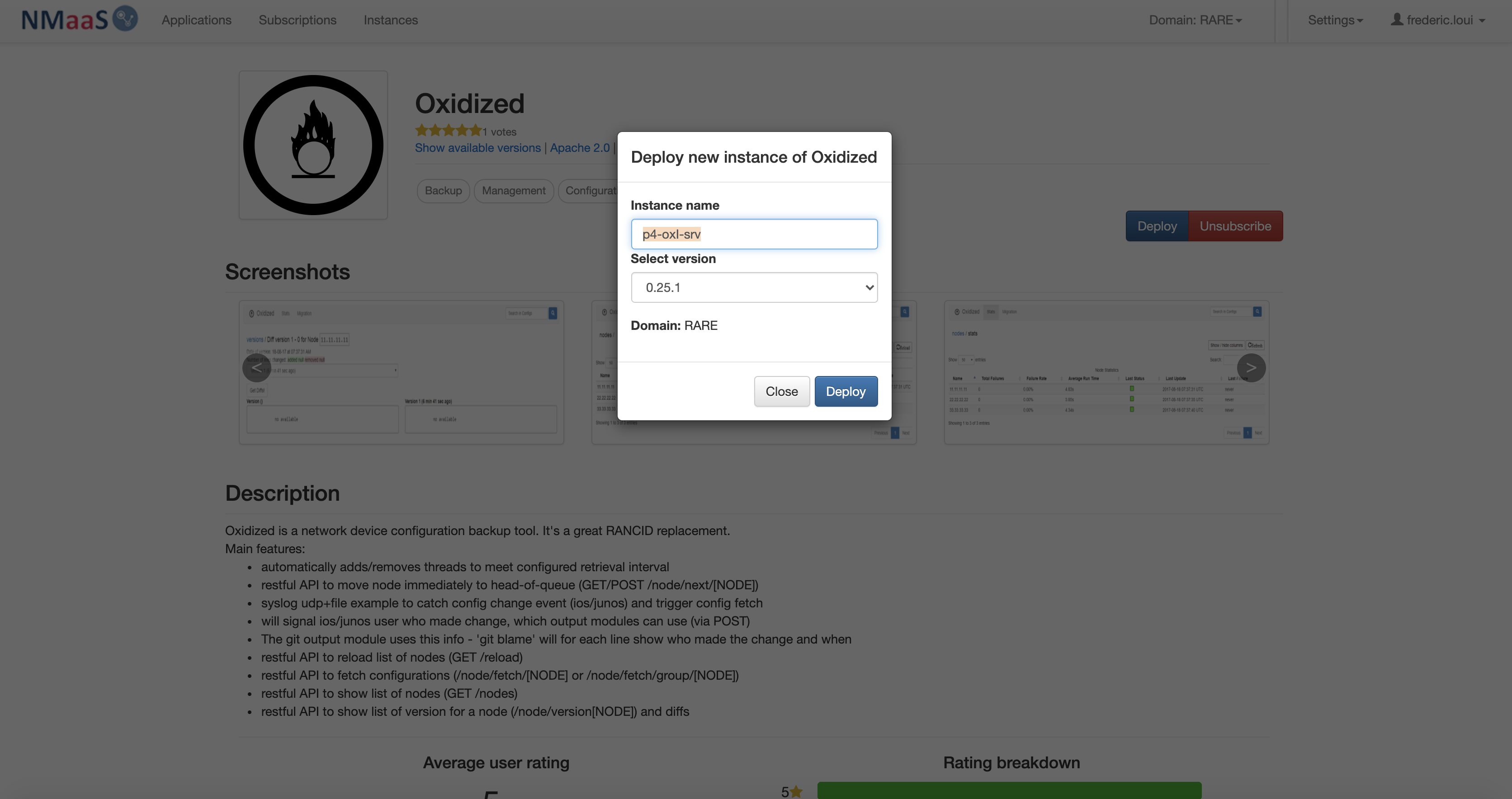
- choose a name for your service instance, in our case we chose: "p4-oxi-srv"
The name has a particular importance as it will dynamically create a FQDN for the NMaaS service in the form: <service_name>.<domain>.nmaas.eu In my example it is: oxidized.rare.nmaas.eu
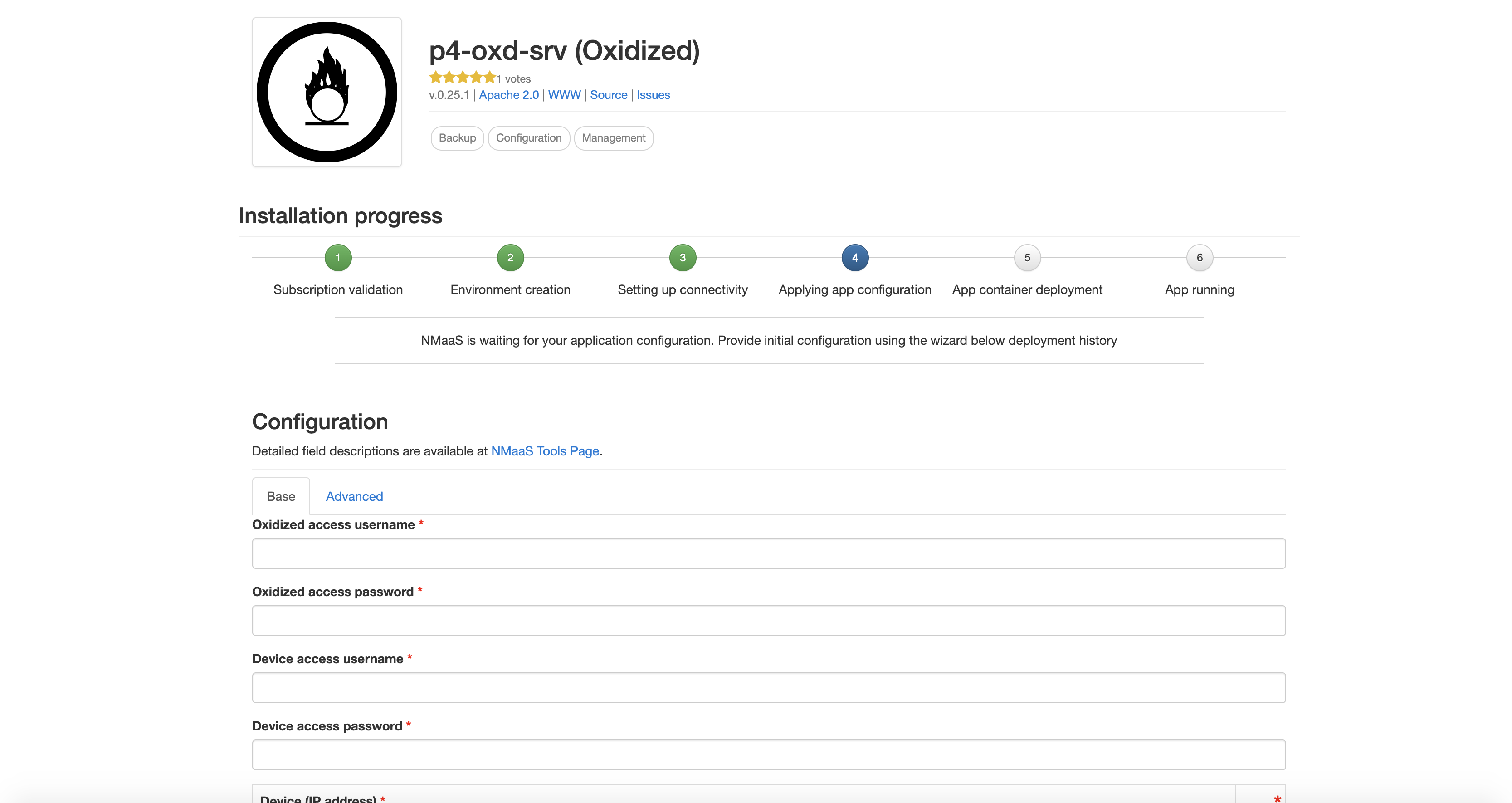
- fill in the mandatory basic configuration information
-
Oxidized access username
we chose: oxidized
-
Oxidized access password
we chose: oxidized
-
Device access username (login used by Oxidized to access the equipment via SSH)
we chose: rare
-
Device access password (password used to access the equipment via SSH)
we chose: rare
-
Device (IP address)
we chose: 172.16.26.103,172.16.26.105,172.16.26.108,172.16.26.109
VPN Connectivity Warning
It is important to note that you'll be connected inside a dedicated VPN so you'll be isolated from the outside world as if you were running your own Out of band management network. So we can assume that your domain is secured.
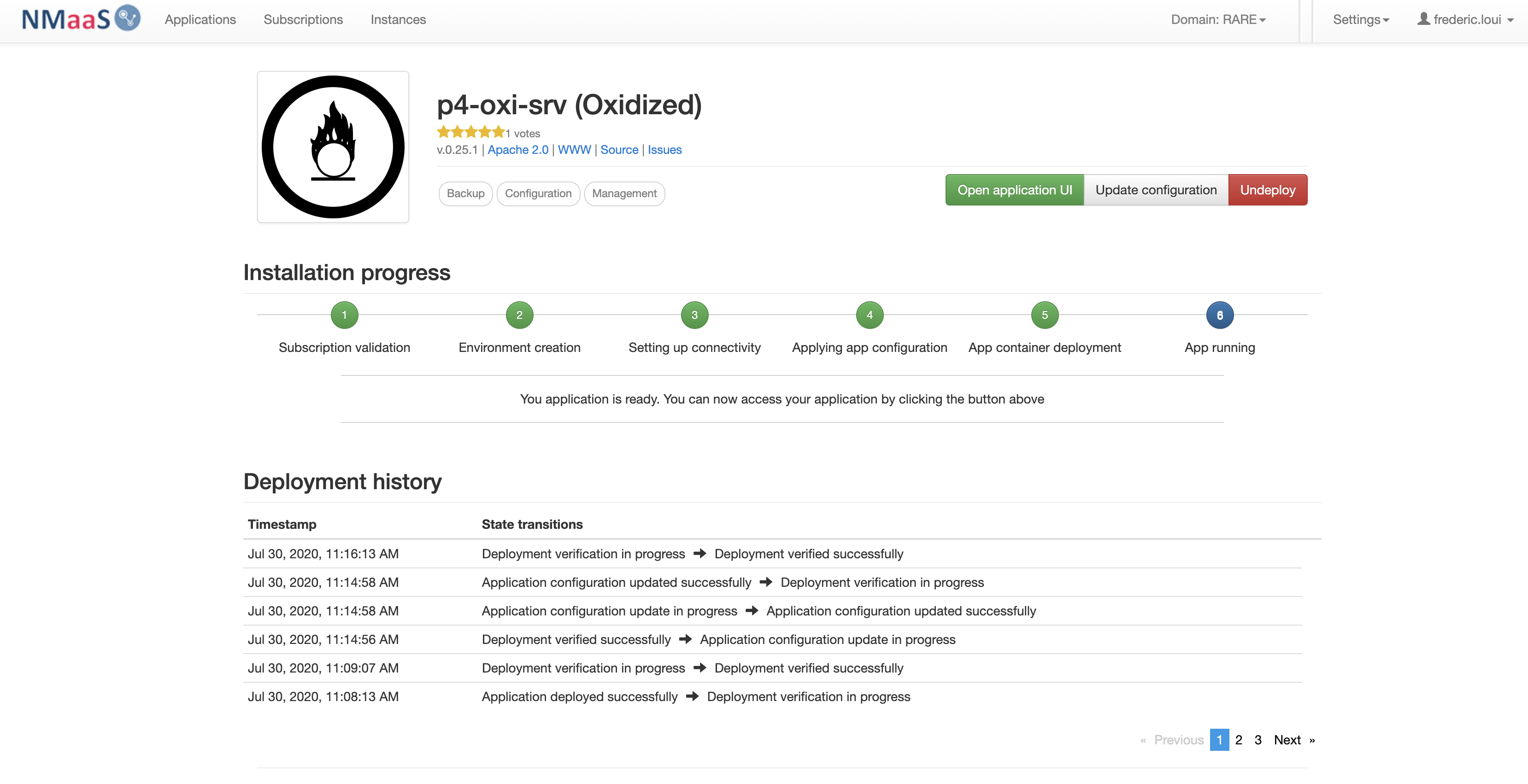
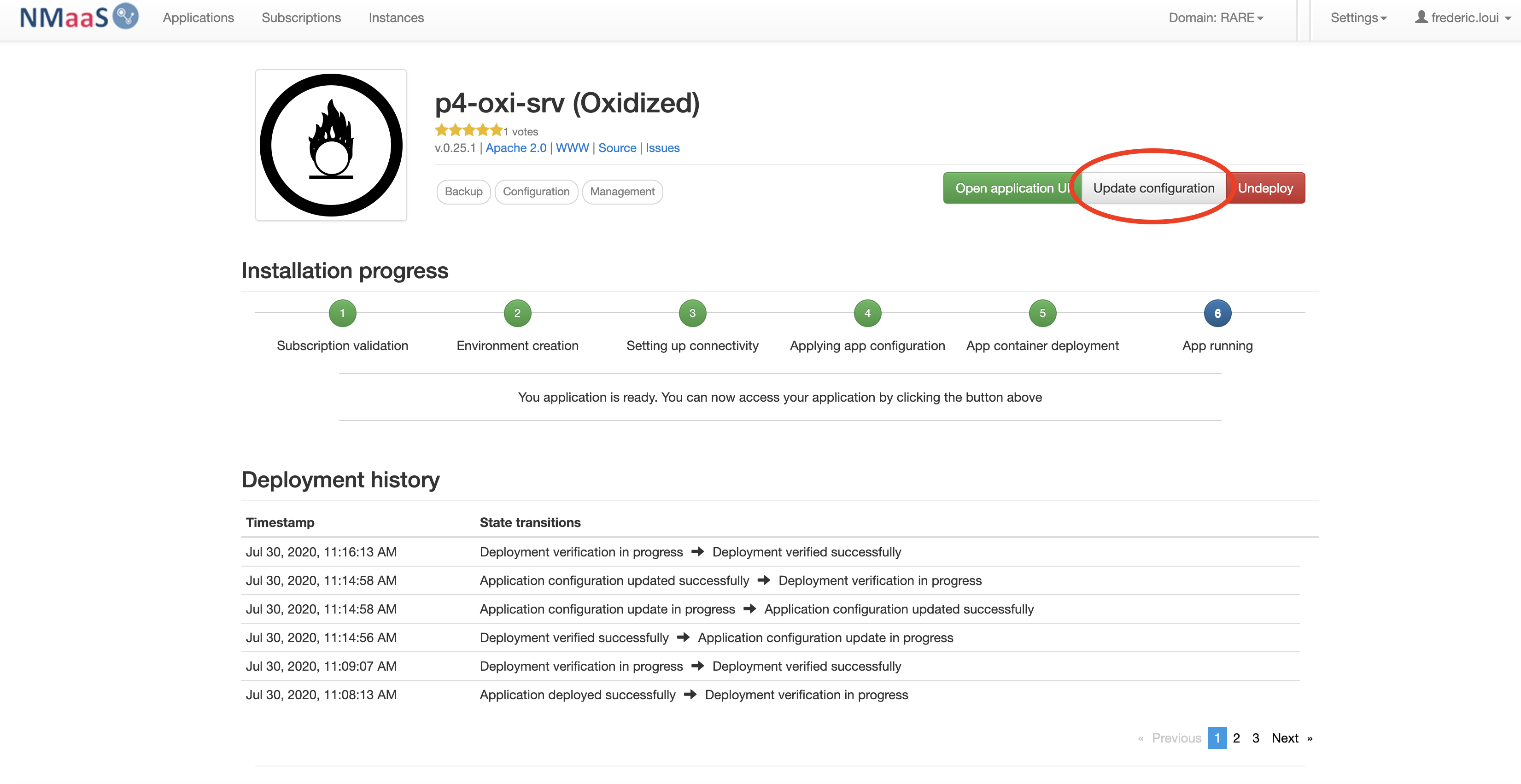
- Congratulation. You should have completed Oxidized deployment
Oxidized application specific configuration
In the RARE domain we had a specific requirement that requires a specific profiles for the RARE network equipment.
We are using then NMaaS configuration feature (also refer to NMaaS configuration process), which actually will provide us the way to alter Oxidized configuration software.
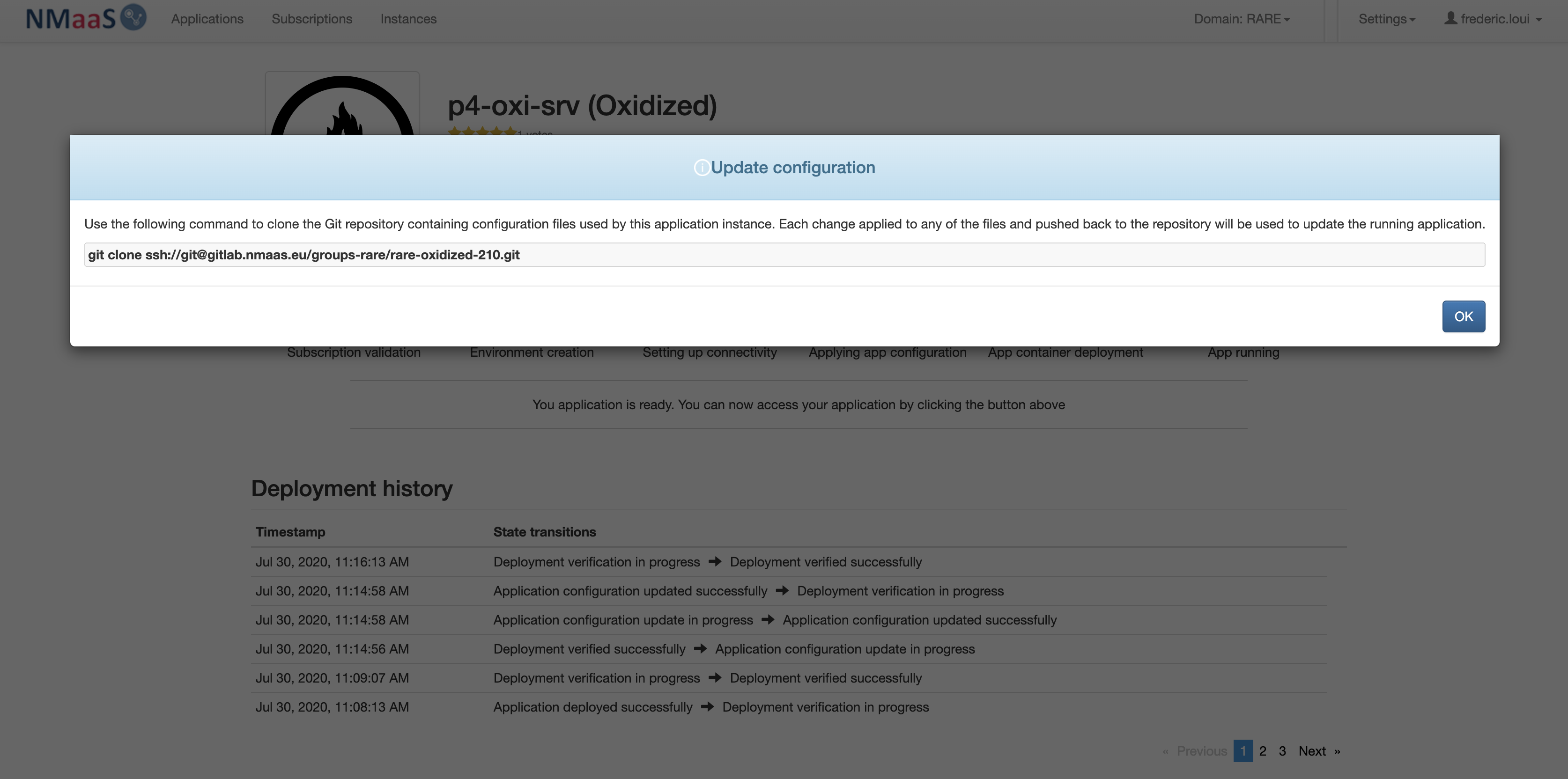
- From the NMaaS portal service instance page select "Update configuration" button
- you should be provided a git command that will let you clone your Oxidized NMaaS configuration repository
| Oxidized base configuration | |
|---|---|
| Oxidized config file sample | |
|---|---|
| |
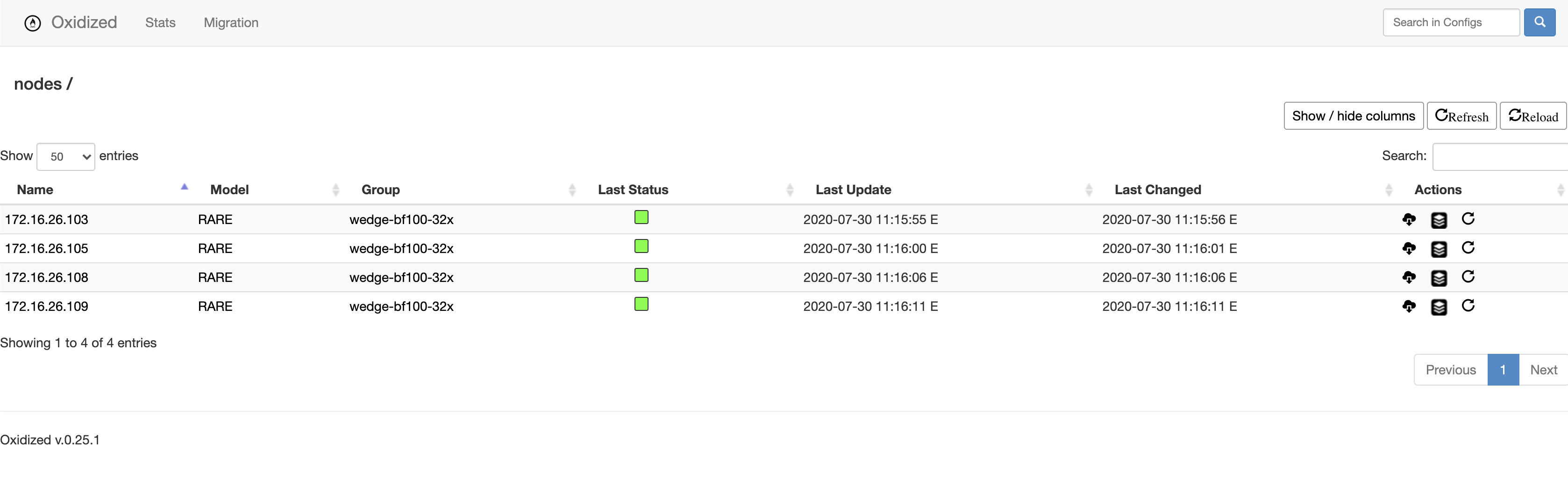
Oxidized router.db file sampl
172.16.26.103:rare:wedge-bf100-32x
172.16.26.105:rare:wedge-bf100-32x
172.16.26.108:rare:wedge-bf100-32x
172.16.26.109:rare:wedge-bf100-32x
| Oxidized model files | |
|---|---|
Oxidized model configuration
Oxidized has the property to associate a model file specific to your equipment. In RARE context we needed to define a specific profile specifying the prompt used and also the command of interest during configuration versioning process.
Verification
Check that you can access Oxidized using: ..nmaas.eu
Congratulations! You have deployed your first NMaaS service specifically for your domain !
Conclusion
In this article you:
- You have deployed a powerful CMDB software for your organisation
- You have learned how to apply specific configurations to it in order to match your requirements
[ #003 ] NMaaS-101 - key take-away
- Deploying a NMaaS service is as easy as deploying an application on your mobile phone, you just have to log into the NMaaS portal and of course have the sufficient privileges to deploy application for your domain
- Deploying an application is a 2 steps process
- deploy the application via the portal
- configure the application via git tool
- Even if Oxidized deployment by NMaaS is made easy, it is mandatory to have a strong knowledge of the tool implemented. In this case, it is of course essential to read documentation from Oxidized GitHub.